IEEE COMSOC VIRTUAL MEETING– 070220–SECURITY IN 5G NETWORKS
| January 5, 2021 | Posted by Frank Gomez under COMSOC, General |
Comments off
|
Subject of Presentation: Security in SDN/NFV and 5G Networks – Opportunities and Challenges
This “Virtual Briefing” was given (with attendees from East Coast to West Coast) to IEEE COMSOC Chapters on Monday evening July 20, 2020.Our on-line presenter was Ashutosh Dutta, Ph.D., who is a Senior Scientist at Johns Hopkins University Applied Physics Lab (JHU/APL), as well an IEEE Communications Society member-At-Large
Of course, we began with the standard 5G pictorial view of the generic goals, as would be provided by the Marketing Group of a telecommunications company.
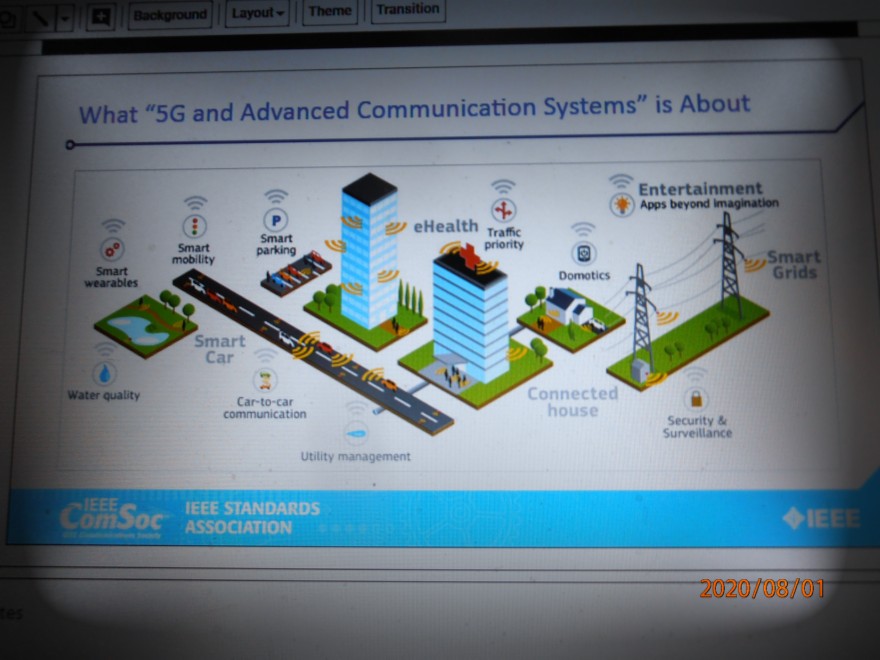
The main emphasis of this talk was to give a view of the topics in communication security that will arise as the 5G stand is developed and deployed. These are the working topics that we in IEEE COMSOC should familiarize ourselves with. They include these grouping: Threat Taxonomy, Security Use Cases and Industry Standards Activities and Testbeds.
The new areas of interest for 5G Security arise from the change in telecommunications from a Traditional Network approach to a Software Defined Network (SDN) /(Network Function Virtualization) NFV Network approach. This change is driven by the use of computer storage “cloud” resources.
As described by our speaker, Traditional Networks were(1) Built using purpose-built hardware coupled with physical connectivity (Ethernet cable connectivity), (2) Control logic largely coordinated and implemented by layers of OSSs, (3) Control, Forward (User) and Data Planes are tightly integrated in Network Elements, and (4) OA&M, inventory views and operational controls managed in OSSs to avoid negative impact to service performance
In turn, now Virtualized Networks are planned with (1) General purpose cloud-based components, (2) Software-based virtual network components and services, (3) Dynamic real-time configuration to support internal or customer activity, and (4) Programmable network management. This means that algorithms must be developed to control service, network usage, and capacity requests by digesting the real time data accumulated analytics
Now our speaker plunged into a detailed list of security challenges in 5G. All of these areas need to be examined and catalogued. They serve as a reference of what situations were proposed. Some of the items listed for attention were: hypervisor vulnerability, API security, orchestration vulnerability, virtual monitoring of virtualized firewalls, maintain security while booting, maintain secure when crashing(now this can expand to a semi-infinity of tests!), user/tenant authentication (probably several hurdles with both static passwords and dynamic passwords that change hourly or daily), topology validation and enforcement, authenticated time service, and private keys within cloud images (presumably encryption within encryption with additional authentication).
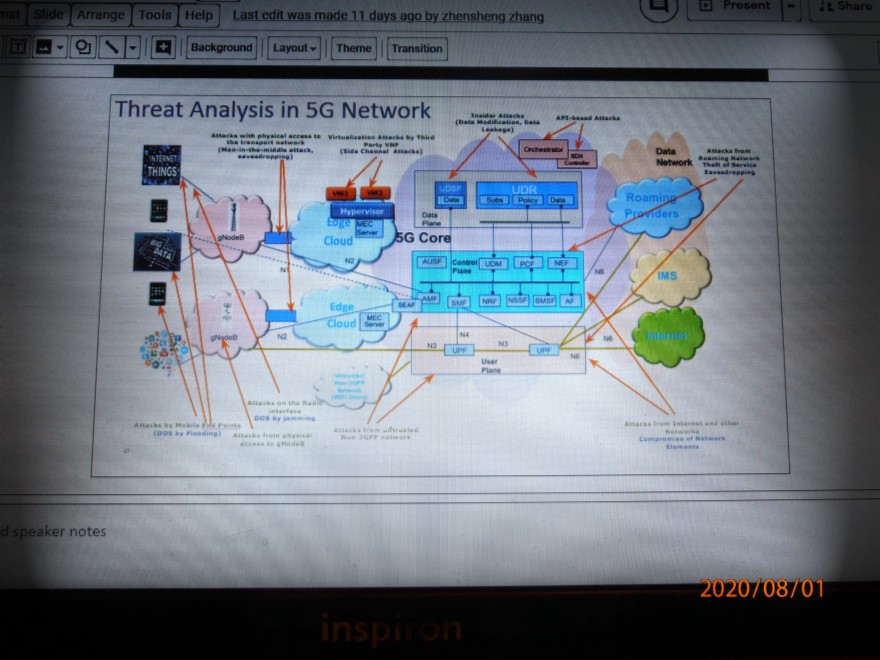
Chart # 17 of Dr A Dutta’s Briefing shows some Initial Threats to a 5G network.
Multiple security attacks potentially envisioned by an adversary are sketched on this busy chart #17.. Another set of attacks may be due to accidental vulnerabilities in the system that were not uncovered in earlier testing.
Looking at this chart, we can gather a number of potential weaknesses and attach points that an adequate security checklist must examine:
- Attacks from multiple end points, such as User Equipment and parts of the multiple of devices that comprise the Internet of Things. Denial Of
- Service by flooding or overloading of requests could result.
- Continuing inability to authenticate that is a legitimate user from the data stream. Attackers crash a network element by sending malformed or garbage packets.
- Attacks on the Radio Access Network RAN interface; DOS by jamming within the matched power receiver band using masked signals.
- Attacks from access to the physical interface gNODeB (Global Node Base)
- Attacks from nodes which have physical access to the transport network. This could involve “eavesdropping” and recording selected filter information that would identify a particular user that an adversary would query. Attackers compromise a network element via a administrative or management interface.
- Virtualization Attacks by Third Party VNF (Side Channel Attack)
- Attacks from untrusted non-3GPP standardized networks
- API-based Attack; APIs are the interfaces defining the communication between applications, controllers and network systems; the API attackers attempt to control the network by searching for a protocol or implementation flaw.
- Attacks from Roaming Network; attempts for theft of service; Eavesdropping
The remainder of the talk dug deeper into similar anticipated attack-security protection with proposing generic security design modifications. The emphasis was that one needs to design a comprehensive review and testing program before one can claim that your 5G system is “secure”.
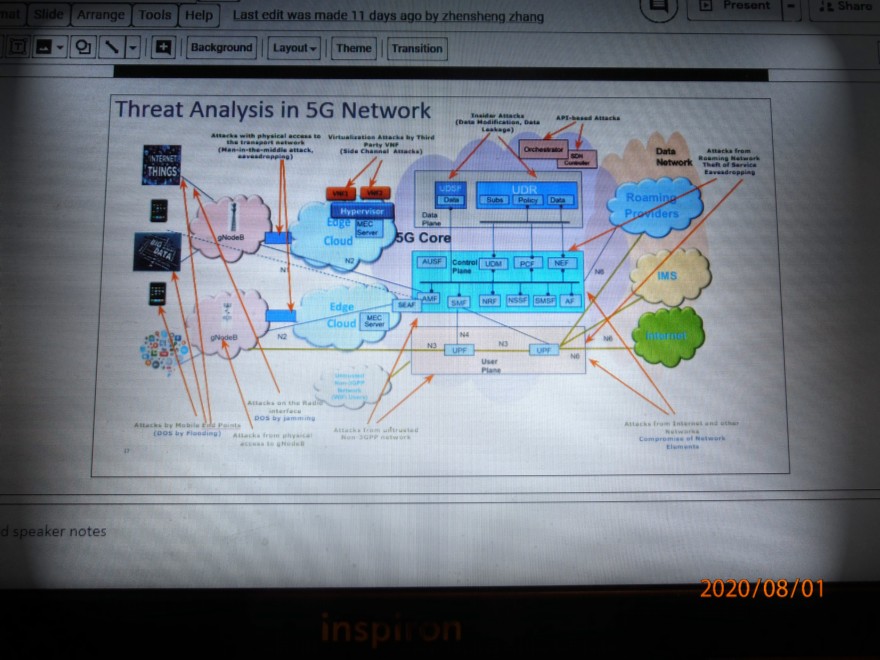
Chart #38 of Dr A Datta’s briefing shows a sample open source testbed.
A discussion on what test beds had been developed, and what the multiple organizations are concentrating their security investigations followed. Lastly, the presenter touched on the related ambitious IEEE Future Networks effort. IEEE members are invited to join and contribute. Contact Dr Ashutosh Datta directly (ashutosh.datta@ieee.org) for more information.
We thank Dr Ashutosh Datta for an excellent presentation in sketching out several areas necessary for a 5GPP system security review. If you are planning to work in this area prepare a detailed roadmap; roll up your sleeves for work; and prepare to present you work to the 5G system developers. Dr Datta has given you many ideas on security issues that need to be examined.
&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&